*This is a living document. We compiled the following tables from publicly available information. Data management companies frequently update their protocols, and while we strive to maintain the most accurate information available, changes may occur.
Safer Tools for Data Management
Data management, including ownership and access, help determine both research and political priorities. While data protocols matter for a wide range of people, the management of Indigenous data directly impacts Indigenous Data Sovereignty (IDS), which “affirms the rights of Indigenous Peoples to control the collection, access, analysis, interpretation, management, dissemination and reuse of Indigenous data”(Walter and Russo 2021: 2; see also CARE Principles for Data Governance). That means creating and using data tools that support Indigenous control and protection over our data, so we can better govern ourselves, our lands, and our Peoples.
Following increasing attacks, including law enforcement requests and concerns over the security and privacy of conventional storage systems (i.e. Google Cloud Platforms, Apple iCloud, Amazon Web Services, and Microsoft Azure), the Indigelab Network (IN) is taking action to identify safer digital tools that better align with Indigenous Data Sovereignty. The implications of unrestrained data access are wide-spread, and may have serious consequences ranging from the weaponization of AI to law enforcement’s use of geofence warrants. The threat to Indigenous funding and research, amongst many Equity, Diversity, and Inclusion (DEI) initiatives, further requires that we as users and creators of data choose more secure data storage tools.
We created the following table(s) to identify more secure alternatives for collaboration, encryption, and file cloud storage. In our roles as Indigenous researchers and community members, our work does not always require high power and fast computing. Rather, we evaluated various data security options with the specific goals of finding safer collaborative data storage tools.
Evaluation Protocol:
We evaluated safe tools based on the following categories:
- Data Security: All recommended tools have meaningful barriers that limit or exclude third party and backdoor access to the data. We recognize that there is a wide spectrum for protecting data from third parties (limiting addresses, closing ports, API security, etc.), but we specifically chose these tools because they are accessible to new users and do not require an extensive technical background.
- Versatility: Everyone has different needs when it comes to data tools. Many of the tools we reviewed offer valuable features such as real-time collaboration, secure sharing of files (documents, spreadsheets, images, videos, etc.), folders secured via protected links and passwords, and remote file deletion.
- Ease of use: All technology has a learning curve. However, we prioritised finding tools that non-specialists can learn with ease. Since many safe tools range in complexity and technical expertise required, our recommendations focus on more accessible, easy to learn, easy to install, and commercially-available products.
- Cost: We’ve prioritized software that is cost accessible. All the options we recommend are either completely free or offer free versions. Additional storage capacity may require additional costs.
Recommended Tools:
Fig 1. Identifying safer digital tools according to their ease of use, jurisdiction, security, and installation type.
| Tool | Use (primary) | Use (secondary) | Ease of use | Country of origin | Security Type | Installation type |
| Cryptpad.fr | Collaborative | File sharing | Easy | France* | E2E; xsalsa20-poly1305 | Web based |
| Sync.com | Encryption | File Storage (cloud) | Easy | Canada* | E2E; AES256 | Either |
| PeaZip | Encryption | File Storage | Medium | Italy*** | AES256 | Local install |
| Nextcloud | File storage | Collaborative | Difficult | Germany*** | E2E; AES256 | Local install |
| Veracrypt | Encryption | File Storage (local) | Medium | France* | AES256 | Local install |
| Proton drive | File storage (cloud) | Encryption | Easy | Switzerland** | E2E; AES | Either |
| Organic Maps | Maps | n/a | Easy | Estonia** | no tracking | Local install |
| Indigenous-owned hosting such as Saltmedia | File storage | File sharing | n/a | Canada* | Web based | |
| *partner in 5, 9, 14 Eyes Alliance , ** Not part of “eyes” alliance, *** part of eyes alliance, but user can select their own server location. | ||||||
Fig 2. Specific purpose and security features of various safer tools
| Feature / Tool | CryptPad | Proton Drive | Nextcloud (DIY Server) | PeaZip | Sync.com |
| Cloud Storage | Yes (limited free plan) | Yes (limited free plan) | Yes (self-hosted) | No cloud storage | Yes (limited free plan) |
| Collaboration Tools | Yes, real-time collaboration on text and data files | No | Yes, real-time collaboration on text and data files | No | No |
| Self-Hosting Option | No | No | Yes – full control over server & data | Not applicable | No |
| File Management | Upload/ download, link sharing | Upload/download, link sharing | Full file management, versioning, sharing | Compression, encryption, file splitting | Upload/download, link sharing |
| Jurisdiction | France | Switzerland | Dependent on hosting location | Local use only | Canada |
| Pricing | Free + paid tiers | Free + paid tiers | Free (self-hosted) | Free | Free + paid tiers |
| Best For | Privacy-first collaboration & office suite. | Secure personal/team file storage | Full-featured private cloud | Local file encryption & compression | Secure personal/ team file storage |
Overall Suggested Uses:
For Collaboration: Cryptpad.fr
- Why Cryptpad.fr: Ease of use that is very similar to Google Workspace or Word. Works well for collaboration and editing.
For Encryption: Peazip OR Sync.com
- Why Peazip: Requires manual installation and manual designation of what files/folders to encrypt. Once encrypted, the user can store and send files securely with further options to add passwords and key files for decryption. More advanced skillset required.
- Why Sync.com: Better option for non-specialists that want secure everyday encrypted cloud storage.
For Storage: Proton Drive OR Nextcloud
- Why Proton Drive: Once a “proton drive” is created the user can store files with robust encryption at every level (metadata, folder structure, etc.). Ideal for minimal start-up cloud storage.
- Why Nextcloud: Preferrable for customizable private self-hosted storage. Server/Operating System software based on Linux. It can act as a self-hosted server for file storage/cloud replacement, collaborative office suite, and includes free personal cloud storage (limited). However, requires advanced technical knowledge for installation and maintenance.
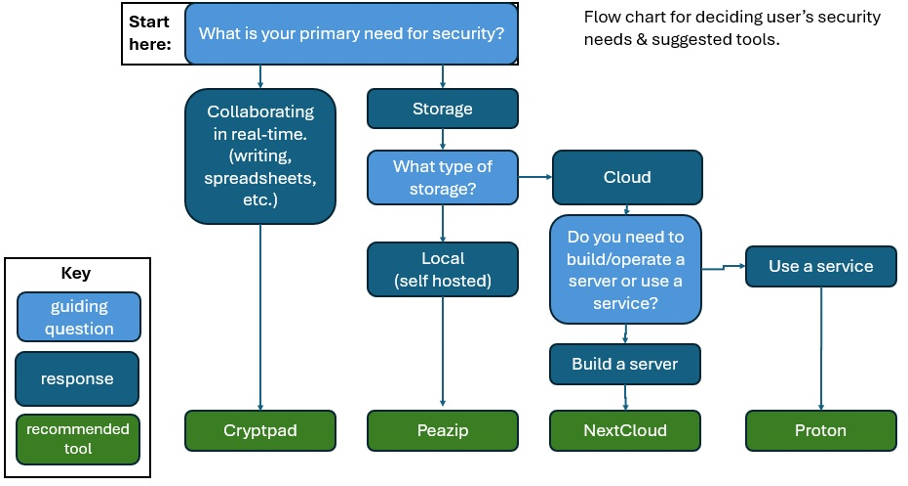
Fig 3. Flow chart for deciding users’ needs and suggested tools.
Contributors:
Thank you to contributors to this project: TR Heydman, Max Liboiron, Veronica Madsen, Shecota Nez, Katherine C. Crocker, Erdanya Anderson, Riley Cotter, Rene L. Begay, Lana Vuleta, Bridget Kakooza, Fernanda Yanchapaxi Travez. Special thanks to all members of the IndigeLab Network’s Indigenous Quantitative Methods Working Group.
Work Cited:
Blue, Violet. n.d. “How to Avoid US-Based Digital Services—and Why You Might Want To.” Wired.
CARE Principles. n.d. Retrieved October 9, 2025. https://www.gida-global.org/care.
Funes, Yessenia. 2025. “Indigenous Scientists Are Fighting to Protect Their Data — and Their Culture.” https://www.theverge.com/features/664282/indigenous-data-sovereignty-native-trump-musk-dei.
Haan, Katherine. 2024. “What Is the Five Eyes Alliance?” Forbes, June 4.
Much Ado About Geofence Warrants. 2018. Retrieved October 9, 2025. https://harvardlawreview.org/blog/2025/02/much-ado-about-geofence-warrants/.
